Creation of a ‘Door to Encryption Technology’ could invite Criminal activity
Encryption Technology UNSW Canberra Cyber Director Nigel Phair says opening up access to encrypted apps to investigate persons of interest[…]
Read moreBusiness Security Systems, Office Security Systems, IT Security Systems

Encryption Technology UNSW Canberra Cyber Director Nigel Phair says opening up access to encrypted apps to investigate persons of interest[…]
Read more
Network Security in the Age of BYOD In recent years, some companies allow their employees to use their personal gadgets[…]
Read more
What a 3D Printed Pelvis can teach us about Network Security Christiaan Beek, is currently a threat hunter and lead[…]
Read more
? Cyber Security – How Far Does Digital Retail Go? With digital technology becoming engrained in every aspect of retail[…]
Read more
Corporate Data Protection A great Video from techrepublic featuring advice on how best to secure your Corporate Data while Traveling.
Read more
The study involved more than 1,000 Americans all over the age of 18. Aside from the 58 percent, 42 percent[…]
Read more
( images source: gannett-cdn.com ) Having Wi-Fi is a must for any fast-moving, digitized workplace. This even extends into industries like[…]
Read more
The landscape of security is constantly changing. New technologies are being invented while some old longstanding traditions are[…]
Read more
ISIS Encryption Technology A Video featuring how ISIS is using the latest Encryption technology to manage their operations and evade[…]
Read more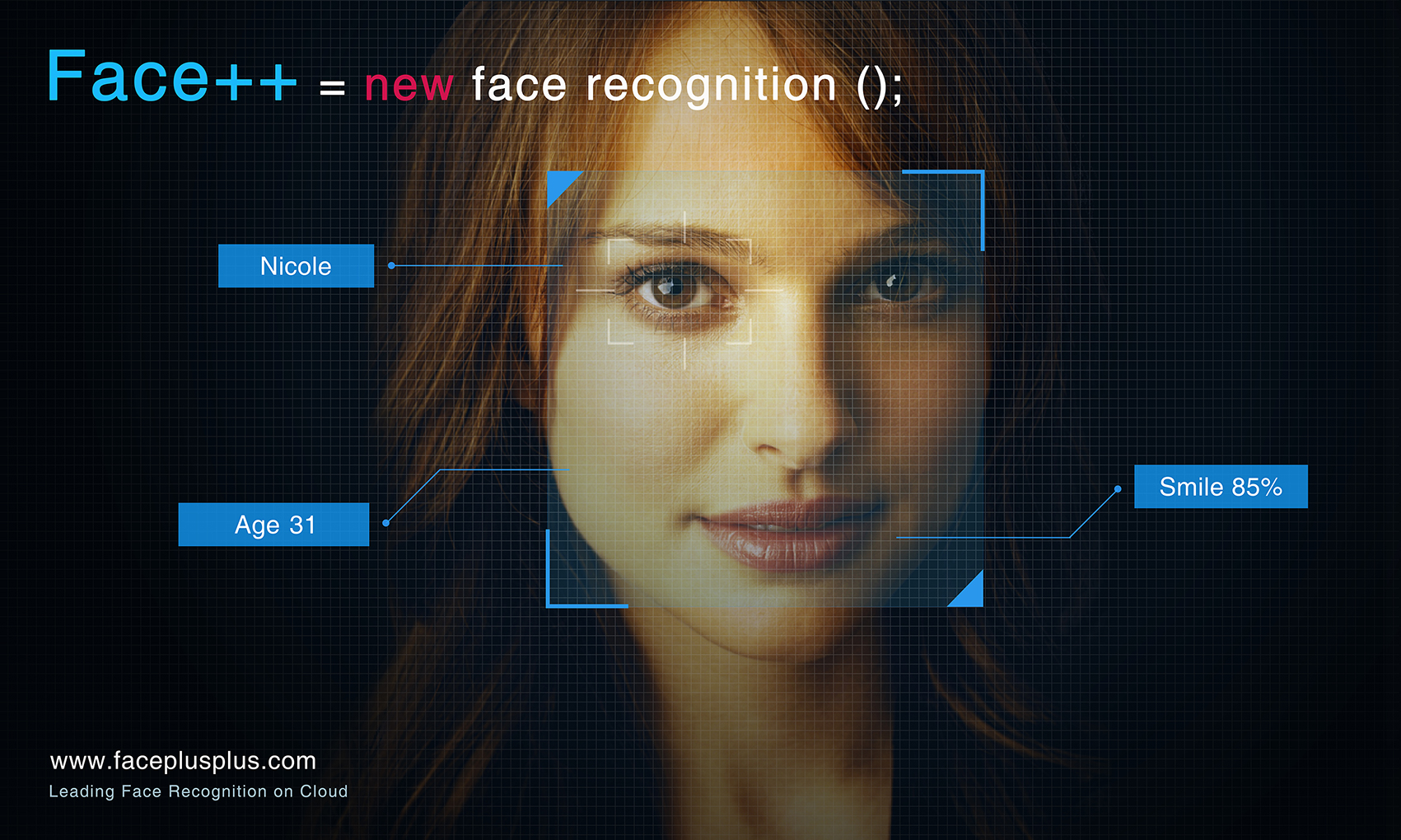
New Facial Recognition Technology An interesting video about new Facial Recognition Technology takes Surveillance to the next Level.
Read more